You may have good reasons to focus on developing your disrupting app. And you may well be a very talented developer. But like me, even after years of experience as a web engineer, comes a point where we have to admit we don't know that much about security.
Unless you only use fully managed solutions to host your web applications, your startup probably has a bunch of servers you have to monitor and maintain. And unless your company has the scale to pay for real DevOps, security engineers, audits or pentests, then quite frankly, we'll mainly focus on finishing the current sprint hoping to get some traction ;)
Today I got my first Ubuntu VPS from OVH, a fresh new image ready to host the next version of my website. And it's got me thinking: I do remember it's best practice to disable SSH login by password, what else should I do ? Do I need a firewall ? Surely I don't have time to fully audit this default Ubuntu image by myself...
In this article I'll show you how to harden a default Ubuntu Server 20.04 image using existing open-source tools:
- Inspec to identify security issues and misconfiguration
- Ansible to automatically harden your server
- The DevSec Hardening Framework which provides:
- An Inspec profile
- Ansible / Chef / Puppet recipes to enforce above Inspec profile
Quick SSH setup
Make sure your server is defined in ~/.ssh/config
Host servername
HostName <your server ip address>
User username
Port 22
To ssh into the server with your ssh key without typing the password just run:
$ ssh-copy-id -i ~/.ssh/id_rsa.pub servername
Using Inspec with linux-baseline profile
On the server:
# download and install Inspec
$ wget https://packages.chef.io/files/stable/inspec/4.20.2/ubuntu/20.04/inspec_4.20.2-1_amd64.deb
$ sudo dpkg -i inspec_4.20.2-1_amd64.deb
# clone the linux-baseline profile
$ git clone https://github.com/dev-sec/linux-baseline
# run the Inspec profile
$ inspec exec linux-baseline
Inspec installation instructions
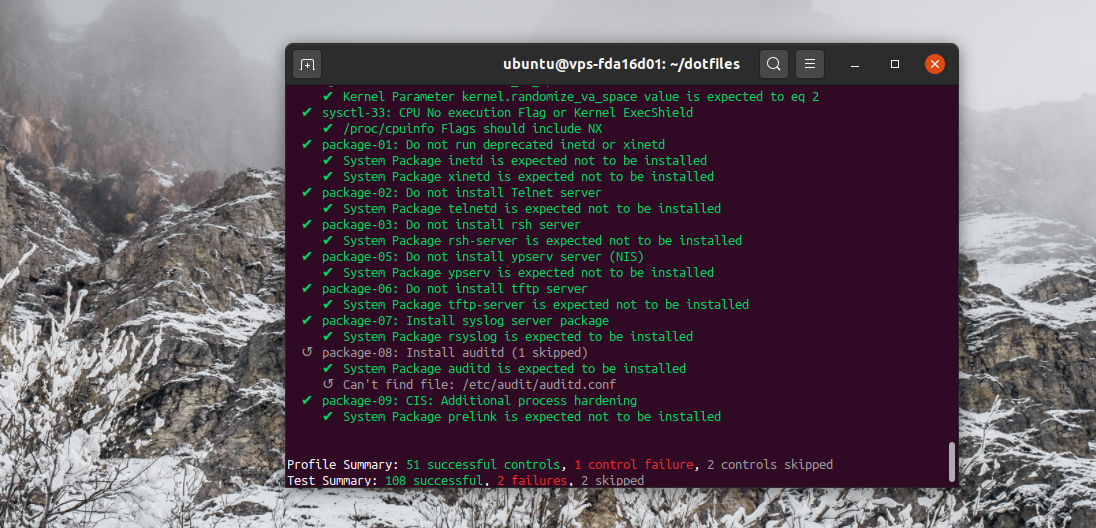
You should see a similar output:
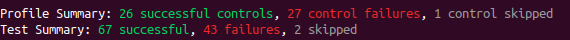
Next thing will be to automatically apply better OS settings using Ansible and the recipes provided by the DevSec framework.
Using Ansible to harden the server
On your local machine:
# install Ansible
$ sudo apt update
$ sudo apt install software-properties-common
$ sudo apt-add-repository --yes --update ppa:ansible/ansible
$ sudo apt install ansible
# install the os and ssh hardening roles
$ ansible-galaxy install dev-sec.os-hardening
$ ansible-galaxy install dev-sec.ssh-hardening
Ansible installation instructions
We then need to write a playbook for each ansible role:
# ansible-os-hardening.yaml
- hosts: your-server
become: true
roles:
- dev-sec.os-hardening
# ansible-ssh-hardening.yaml
- hosts: your-server
become: true
roles:
- dev-sec.ssh-hardening
Finally run these playbooks with the following commands:
$ ansible-playbook -K ansible-os-hardening.yaml
$ ansible-playbook -K ansible-ssh-hardening.yaml
Then, re-running inspec exec linux-baseline on the server should give a similar output:
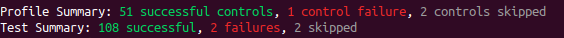
Which is much better!
Final thoughts
Though I can't say I have audited the DevSec framework per-se, I hope you now have a better understanding on how you can automate your servers security to stay up-to-date whith industry best practices.
Depending on what you then run on your server, you may have to allow some ports on the Ubuntu firewall, ufw. Personally while testing CapRover I just had to run:
$ ufw allow 80,443,3000,996,7946,4789,2377/tcp; ufw allow 7946,4789,2377/udp;